Cybersecurity is becoming the biggest concern for organizations and business setups. More criminals are focused on cybercrimes and upgrading their skills and expertise to launch attacks and access the data and resources of organizations. It has also made the authorities conscious of their security practices. A little vulnerability can cause a huge loss to the setup and sabotage its reputation too.
Penetration testing is an ethical hacking in which organizations allow experts to launch cyber-attacks imitating the behavior and pattern of criminals. The purpose is to identify the security loopholes and address them efficiently to mitigate the risks of actual attacks. There are different types of penetration testing, and organizations can opt for one according to their suitability.
Keep reading this article explain different penetration testing types businesses should know about and strengthen their cybersecurity.
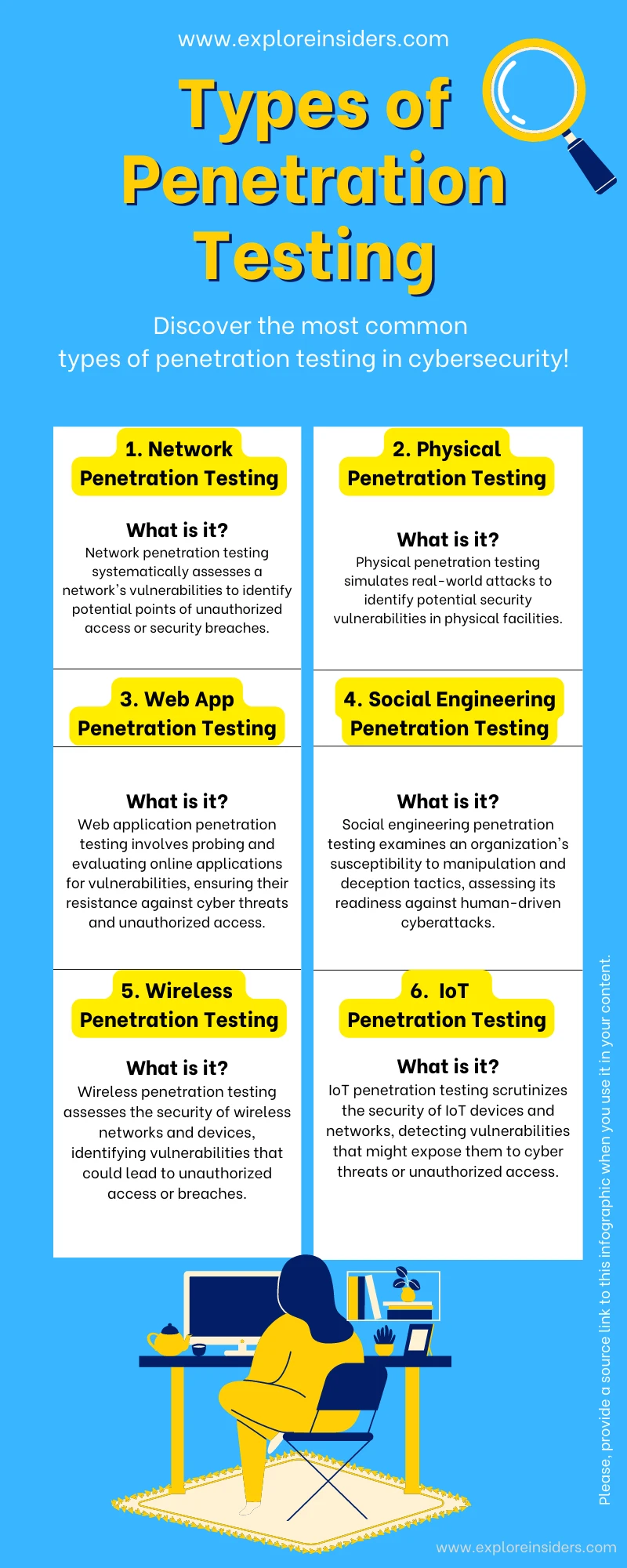
Top 6 Types of Penetration Testing Businesses Must Know
The networks in a business organization are exposed to various threats and risks. A significant number of such risks arise due to vulnerabilities and loopholes in network security. Identifying and fixing them is crucial to strengthen overall security. Opting for the right type of penetration testing is the right approach to identifying the issues and developing strategies to bridge the gap in security and stay alert for future threats and vulnerabilities.
Here are the most notable types of penetration testing businesses must know about and implement to optimize their security.
1. Network Penetration Testing
Network penetration testing is the first and foremost type organizations should be aware of. Such testing is focused on identifying vulnerabilities and security loopholes in the network infrastructure. It can include servers, switches, firewalls, etc. Network penetration testing is necessary to save the business from proxy server attacks, database attacks, firewall misconfiguration, or bypass and router attacks. However, not anyone but experts only can conduct the testing. Many organizations hire penetration testing companies to let experts conduct thorough testing and fix security vulnerabilities efficiently.
2. Physical Penetration Testing
Physical penetration testing is the next notable type every business organization must know about. The physical controls of a setup which include sensors, cameras, locks, and doors, might have compromised security and loopholes. These can offer access to the server rooms and other sensitive areas of the facility while compromising the security of the whole network. Physical security vulnerabilities can negatively impact the customers and partnerships of the business. Penetration testing can offer support against tailgating, badge cloning, and social engineering threats.
3. Web Application Penetration Testing
Web application penetration testing is the next major type business entities should know about. As the name suggests, such penetration testing focuses on catching vulnerabilities in web-based applications. It can be used to identify loopholes in source doses, databases, and the backend networks. It also offers significant support in mitigating vulnerabilities and long-term security solutions. Reconnaissance, discovery, and attack are the essential step you can follow to conduct web-application penetration testing smoothly and draw favorable results.
4. Social Engineering Penetration Testing
Social engineering penetration testing is another crucial type in the current times. Such penetration testing focuses on the security vulnerabilities linked to people and processes in the organization. They are often deemed as the weakest link and ignored from the security point of view, which is not the right approach. On the other hand, attackers and criminals are always on the lookout for the slightest loophole, and they fully misuse it. Social engineering penetration testing allows authorities to use ethical hacking and identify vulnerabilities in spoofing, phishing, and dropping USBs. It can help develop security awareness pathways and strengthen it.
5. Wireless Penetration Testing
It is another common type every business organization should be aware of. Wireless communication has become the norm for business setups at internal and external levels. The data flows in and out of the networks, which exposes it to numerous vulnerabilities and loopholes. Unauthorized access and data exfiltration are the biggest risks associated with it. Wireless penetration testing identifies the associated risk and weaknesses and helps strengthen security. Businesses can use it to identify risks like session reuse, wireless router misconfiguration, de-authentication attacks, and unauthorized wireless devices.
6. IoT Penetration Testing
IoT penetration testing is the last type every business organization should be aware of. This type of penetration testing targets and identifies vulnerabilities and loopholes in the connected ecosystem. The hardware, communication protocols, embedded software, servers, and web and mobile applications linked to the IoT devices can have security vulnerabilities. The experts will opt for a specific test according to the connected device to identify and fix the vulnerabilities. You can also hire penetration testing companies and rely on experts to identify and fix all the issues and uphold your security.
Do You Lack the Expertise to Conduct Penetration Testing?
It’s best to trust experts when it comes to conducting penetration testing and mitigating security risks, especially if you lack the necessary skills and expertise. Feel free to consult with professional penetration testing companies in UAE and fix all the loopholes in your network security and protect your setup from cyber-attacks.